Subnets
Every Cyber Ranges environment will have at least one Subnet (apart form the AdminBox subnet) which range Systems can be launched into. You can also add new subnets, modify the security rules for existing subnets, and delete existing subnets.
This provides a ton of flexibility when it comes to the networking setup of your range environments.
Existing Template NetworkingBe careful when modifying the networking rules for existing range templates! Systems and software may be configured which rely on the current networking rules. These may break if changes are applied.
Subnet information can be found for each range under the Settings page within the Subnets tab. At a glance you can see your subnets, their network ranges, and how many network interfaces reside in each.
Adding Subnets
To add a Subnet to your range, select the + Subnets button. Provide a Name, Description, and Network Range for the subnet. The Network Range provided must be valid CIDR format, reside within your range's overall network parameters, and not conflict with any existing subnets.
You can modify the security rules of the subnet before or after it's created.
Modifying Security Rules
Security Rules control what network traffic can flow into, and out of, the subnet. These security rules are specific to Cyber Ranges/AWS and don't necessarily align with standard firewall or Network ACL behavior. For more details on Security rule specifics, red the AWS User Guide on the topic.
VPN Client IP vs AdminBox IP
- AdminBox Interfaces vs. VPN Client IPs: There are two IP addresses associated with VPN connections. VPN Client IPs (e.g. 10.9.253.0/24 and 10.9.254.0/24) and AdminBox Interfaces (e.g. 10.10.255.244 and 10.10.0.4). These IPs may vary depending on the lab network range.
- Security Group Evaluation: For security group evaluation, AWS uses the AdminBox Interface for traffic within the same subnet (e.g. 10.10.0.X -> 10.10.0.X). For traffic between subnets, AWS uses the VPN Client IPs (e.g. 10.10.0.X -> 10.10.255.X).
These are important distinctions for creating inbound and outbound security rules that behave as you expect, so please bear them in mind while you design your range!
To create or modify a rule, you'll need to select the following:
- Protocol
- Port Range
- Source/Destination CIDR
- Description (Optional)
Below is a set of inbound and outbound security rules, as an example:
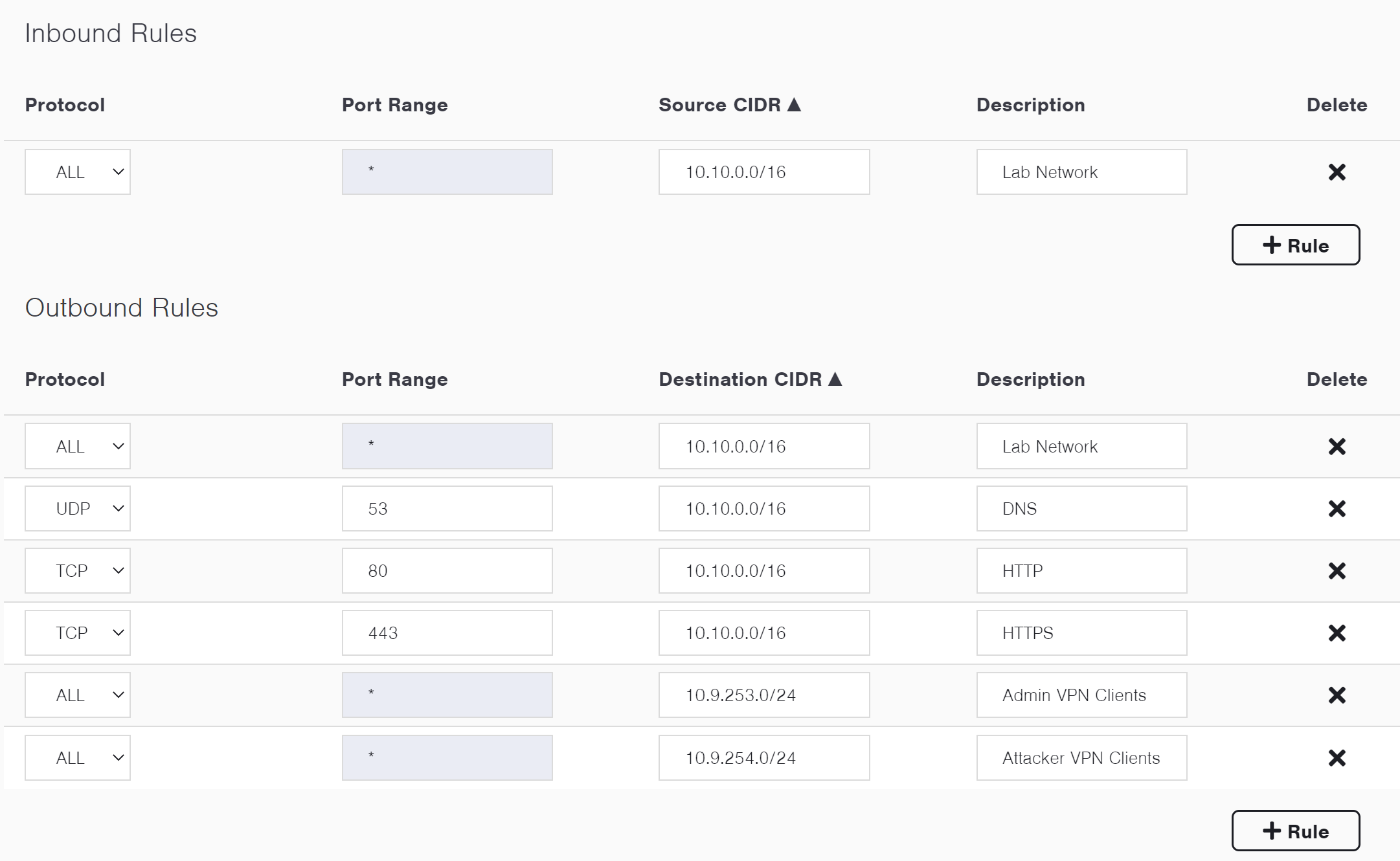
Example Security Group Rules
Deleting Subnets
To delete a subnet, it must not contain any Network Interfaces. Before deleting a subnet, first delete any secondary network interfaces associated with it, or delete the system itself for primary interfaces.
Once you've removed any associated interfaces you can delete the subnet by selecting the delete icon.
Updated 10 months ago